







All Resources
Filtered By
"User Input"
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

13 Mar 2024
Whitepapers
Kubernetes Security Master Guide Download
This Kubernetes Security Master Guide downloadable PDF provides invaluable insights and strategies to protect your Kubernetes deployments.

March 13, 2024
Whitepapers
Kubernetes Security Master Guide Download
This Kubernetes Security Master Guide downloadable PDF provides invaluable insights and strategies to protect your Kubernetes deployments.

12 Mar 2024
Press
RAD Security Renames to RAD Security, Reflecting Broadened Scope in Behavioral Detection & Response
RAD Security is renaming as RAD Security, reflecting expanded scope in behavioral cloud native detection and response

March 12, 2024
Press
RAD Security Renames to RAD Security, Reflecting Broadened Scope in Behavioral Detection & Response
RAD Security is renaming as RAD Security, reflecting expanded scope in behavioral cloud native detection and response

09 Mar 2024
Whitepapers
Kubernetes Security Best Practices Checklist
This Kubernetes security checklist is your first line of defense against common vulnerabilities and threats.

March 9, 2024
Whitepapers
Kubernetes Security Best Practices Checklist
This Kubernetes security checklist is your first line of defense against common vulnerabilities and threats.

29 Feb 2024
Whitepapers
Cloud Native Identity Threat Detection & Response (ITDR) Checklist
If you want to detect and respond to any compromises of the Kubernetes RBAC identities across your environment, you will need to ensure any tool you use can match this identity threat detection and response checklist.

February 29, 2024
Whitepapers
Cloud Native Identity Threat Detection & Response (ITDR) Checklist
If you want to detect and respond to any compromises of the Kubernetes RBAC identities across your environment, you will need to ensure any tool you use can match this identity threat detection and response checklist.

29 Feb 2024
Webinars
Hands-On Workshop: Kubernetes RBAC Right-Sizing and Secure Coding Access Control with Jimmy Mesta & Jim Manico
Do you want to get ahead with secure coding practices for access control? Do you need to add Kubernetes RBAC to your zero trust initiatives? Join our two hour workshop to get hands on.

February 29, 2024
Webinars
Hands-On Workshop: Kubernetes RBAC Right-Sizing and Secure Coding Access Control with Jimmy Mesta & Jim Manico
Do you want to get ahead with secure coding practices for access control? Do you need to add Kubernetes RBAC to your zero trust initiatives? Join our two hour workshop to get hands on.
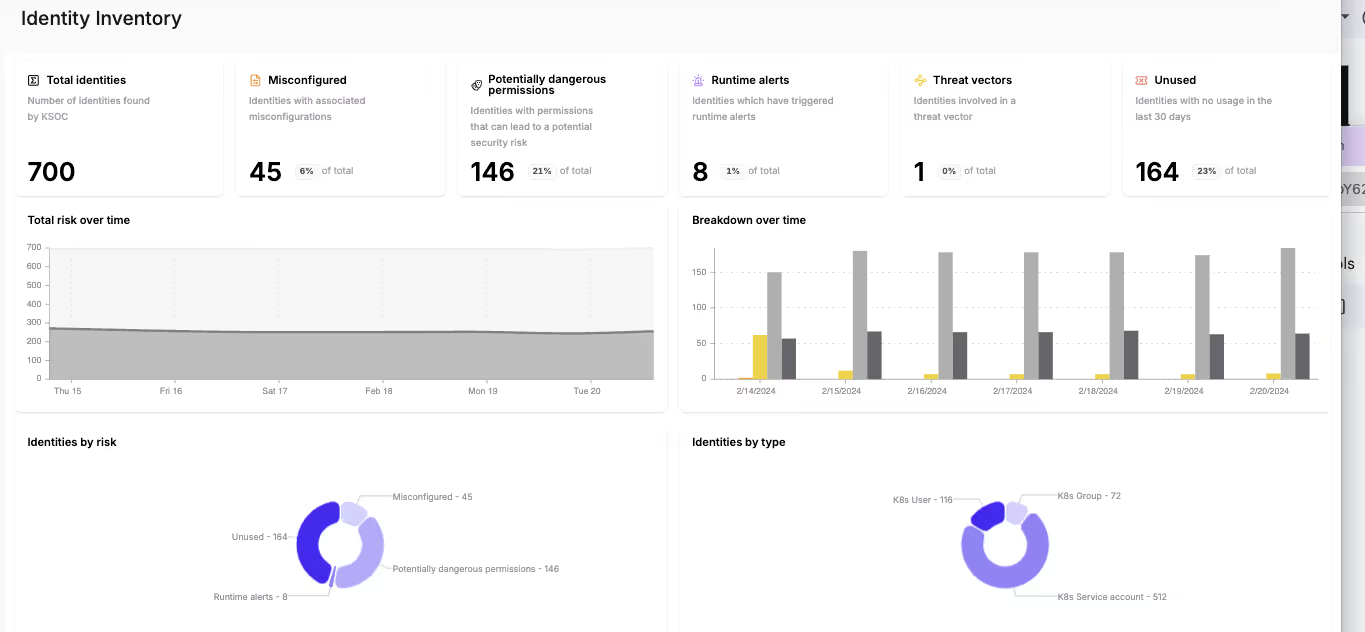
27 Feb 2024
Press
RAD Security releases first zero trust RBAC policy generator
Kubernetes Security Operations Center (RAD Security) is announcing the first Kubernetes RBAC zero trust policy generator

February 27, 2024
Press
RAD Security releases first zero trust RBAC policy generator
Kubernetes Security Operations Center (RAD Security) is announcing the first Kubernetes RBAC zero trust policy generator

06 Feb 2024
Webinars
Hands-On Workshop: Kubernetes Red Team / Blue Team Exercise
RAD Security hosts a red team / blue team workshop walking through detection and response of Kubernetes attacks.

February 6, 2024
Webinars
Hands-On Workshop: Kubernetes Red Team / Blue Team Exercise
RAD Security hosts a red team / blue team workshop walking through detection and response of Kubernetes attacks.
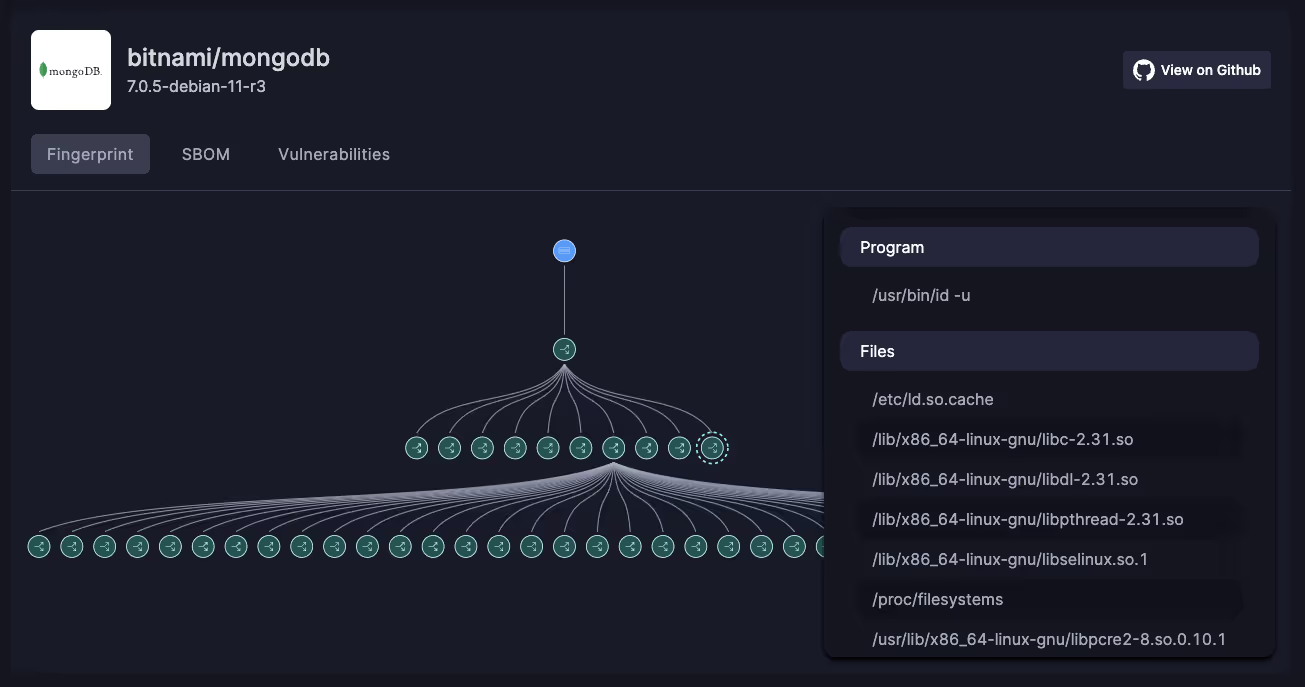
30 Jan 2024
Press
RAD Security releases first verifiable runtime fingerprint standard
Kubernetes Security Operations Center (RAD Security) is announcing the first verified cloud native workload fingerprint

January 30, 2024
Press
RAD Security releases first verifiable runtime fingerprint standard
Kubernetes Security Operations Center (RAD Security) is announcing the first verified cloud native workload fingerprint

29 Jan 2024
Webinars
Pass the Hot Potato: Who Should Take Hold of K8s Security?
In this webinar, you'll learn the parts of Kubernetes Security that are ideal for Security versus engineering. Plus, get a special preview of the Security Hub talks at Kubecon!

January 29, 2024
Webinars
Pass the Hot Potato: Who Should Take Hold of K8s Security?
In this webinar, you'll learn the parts of Kubernetes Security that are ideal for Security versus engineering. Plus, get a special preview of the Security Hub talks at Kubecon!

06 Dec 2023
Webinars
Kubernetes Targeted Attacks in 2023: How to Detect & Respond
How to protect against the tactics of the four main Kubernetes-targeted attacks, including the Dero and Monero cryptocurrency mining campaigns, Scarleteel and RBAC-Buster.

December 6, 2023
Webinars
Kubernetes Targeted Attacks in 2023: How to Detect & Respond
How to protect against the tactics of the four main Kubernetes-targeted attacks, including the Dero and Monero cryptocurrency mining campaigns, Scarleteel and RBAC-Buster.

18 Nov 2023
Whitepapers
Comparing Rad Security to OPA
Find out how Rad Security provides the context to operationalize OPA-compatible admission control for Kubernetes.

November 18, 2023
Whitepapers
Comparing Rad Security to OPA
Find out how Rad Security provides the context to operationalize OPA-compatible admission control for Kubernetes.

18 Nov 2023
Whitepapers
A Checklist for Evaluating a Kubernetes Admission Controller
Here is a checklist to help you rate vendors’ Kubernetes admission control options and understand whether you are getting something useful, or something you will pay for but never operationalize.

November 18, 2023
Whitepapers
A Checklist for Evaluating a Kubernetes Admission Controller
Here is a checklist to help you rate vendors’ Kubernetes admission control options and understand whether you are getting something useful, or something you will pay for but never operationalize.

07 Nov 2023
Press
RAD Security launches AI-powered Cloud-Native Identity Threat Detection
Kubernetes Security Operations Center (RAD Security) is announcing the first AI-powered Cloud-Native Identity Threat Detection platform.

November 7, 2023
Press
RAD Security launches AI-powered Cloud-Native Identity Threat Detection
Kubernetes Security Operations Center (RAD Security) is announcing the first AI-powered Cloud-Native Identity Threat Detection platform.

10 Oct 2023
Whitepapers
Kubernetes Security Visibility Checklist
Download the Kubernetes Security Checklist for enhanced visibility beyond hardening measures and admission control policies in your Kubernetes environment.

October 10, 2023
Whitepapers
Kubernetes Security Visibility Checklist
Download the Kubernetes Security Checklist for enhanced visibility beyond hardening measures and admission control policies in your Kubernetes environment.

09 Oct 2023
Whitepapers
Kubernetes Security Posture Management Misconfigurations (KSPM)
Download our KSPM whitepaper which covers the common Kubernetes misconfigurations to look out for, as well as how to use KSPM for accomplishing a broader set of security functions within your Kubernetes environment.

October 9, 2023
Whitepapers
Kubernetes Security Posture Management Misconfigurations (KSPM)
Download our KSPM whitepaper which covers the common Kubernetes misconfigurations to look out for, as well as how to use KSPM for accomplishing a broader set of security functions within your Kubernetes environment.

15 Sep 2023
Webinars
Tips for Improving Cloud Native Security Efficiency | Cloud Native Security 30-Minute Webinar
Cloud Native Security: Join Dineshwar Sahni and RAD Security CMO, Story Tweedie-Yates, for a webinar on practical tips to combat burnout and meet the evolving demands of cloud native security.

September 15, 2023
Webinars
Tips for Improving Cloud Native Security Efficiency | Cloud Native Security 30-Minute Webinar
Cloud Native Security: Join Dineshwar Sahni and RAD Security CMO, Story Tweedie-Yates, for a webinar on practical tips to combat burnout and meet the evolving demands of cloud native security.

05 Sep 2023
Customer Stories
ActBlue chooses RAD Security to secure billions in online transactions through Kubernetes
ActBlue chooses RAD Security to secure its Kubernetes security environment which manages billions in online transactions.

September 5, 2023
Customer Stories
ActBlue chooses RAD Security to secure billions in online transactions through Kubernetes
ActBlue chooses RAD Security to secure its Kubernetes security environment which manages billions in online transactions.

31 Aug 2023
Whitepapers
The Defender's Guide to Protecting Against Kubernetes Attacks in 2023
This white paper compares common methods of protection against attackers' tactics used in the four Kubernetes attacks in 2023. Download it today!

August 31, 2023
Whitepapers
The Defender's Guide to Protecting Against Kubernetes Attacks in 2023
This white paper compares common methods of protection against attackers' tactics used in the four Kubernetes attacks in 2023. Download it today!
No resources match your criteria.



