RAD Insights









Featured
.png)
January 29, 2026
Inside FusionAI: Getting Signal from your Stack with RADBot
FusionAI powers RADBot to reason across cloud, Kubernetes, and identity data, delivering explainable security answers teams can act on fast.

January 29, 2026
Inside FusionAI: Getting Signal from your Stack with RADBot
FusionAI powers RADBot to reason across cloud, Kubernetes, and identity data, delivering explainable security answers teams can act on fast.
.png)
December 10, 2025
How RAD Helps Teams Answer the Only Question That Matters: Are We Exposed? Operational lessons from React2Shell and Shai Hulud, and how RAD closes the visibility gap.
React2Shell and Shai Hulud show how fast teams need to answer: Are we exposed? Learn how RAD helps security teams cut through noise, correlate runtime signals, and get real answers—without waiting for the CVE.

December 10, 2025
How RAD Helps Teams Answer the Only Question That Matters: Are We Exposed? Operational lessons from React2Shell and Shai Hulud, and how RAD closes the visibility gap.
React2Shell and Shai Hulud show how fast teams need to answer: Are we exposed? Learn how RAD helps security teams cut through noise, correlate runtime signals, and get real answers—without waiting for the CVE.
.png)
November 5, 2025
Introducing the New RAD Platform & RAD FusionAI
RAD has been rebuilt from the inside out to make security work clear, fast, and verifiable. The new RAD Platform unifies data, reasoning, and action in one explainable system—security that finally makes sense.

November 5, 2025
Introducing the New RAD Platform & RAD FusionAI
RAD has been rebuilt from the inside out to make security work clear, fast, and verifiable. The new RAD Platform unifies data, reasoning, and action in one explainable system—security that finally makes sense.
.png)
October 14, 2025
The Cost of “Cosmetic” AI: Why GPT Wrappers Drain More Than They Deliver
Many “agentic AI” tools are just polished wrappers—repackaging your data without reducing real work. Learn how to tell the difference between cosmetic AI and systems that truly close the loop.

October 14, 2025
The Cost of “Cosmetic” AI: Why GPT Wrappers Drain More Than They Deliver
Many “agentic AI” tools are just polished wrappers—repackaging your data without reducing real work. Learn how to tell the difference between cosmetic AI and systems that truly close the loop.
All Insights
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.

June 24, 2024
A Brief History of Signature-Based Threat Detection in Cloud Security
What are signatures as they relate to security threats in the cloud? Use the history of signature-based ips/ids threat detection and EDR to find out

June 24, 2024
Story Tweedie-Yates
A Brief History of Signature-Based Threat Detection in Cloud Security
What are signatures as they relate to security threats in the cloud? Use the history of signature-based ips/ids threat detection and EDR to find out
Cloud-Native Security
Detection and Response

May 22, 2024
Guide to Threat Detection and Response in Cloud Environments
Effective threat detection aims to identify suspicious activities early, while coordinated response actions reduce the impact of these threats.

May 22, 2024
RAD Security
Guide to Threat Detection and Response in Cloud Environments
Effective threat detection aims to identify suspicious activities early, while coordinated response actions reduce the impact of these threats.
Detection and Response

May 20, 2024
Cloud Security Monitoring, Management, and Compliance Basics
Cloud Security Monitoring, Management, and Compliance are three pillars that work together to make cloud operations safe and protect organizations against security breaches.

May 20, 2024
RAD Security
Cloud Security Monitoring, Management, and Compliance Basics
Cloud Security Monitoring, Management, and Compliance are three pillars that work together to make cloud operations safe and protect organizations against security breaches.
Cloud-Native Security Basics

May 5, 2024
What is Behavior-Based Threat Detection and Response in a Cloud-Native Environment?
Learn what behavioral threat detection and response looks like in cloud-native environments instead of legacy, monolithic and cloud environments

May 5, 2024
Story Tweedie-Yates
What is Behavior-Based Threat Detection and Response in a Cloud-Native Environment?
Learn what behavioral threat detection and response looks like in cloud-native environments instead of legacy, monolithic and cloud environments
Cloud-Native Security
Detection and Response
RAD Security Standard

April 29, 2024
What is Cloud Security Posture Management (CSPM) and Why Does It Matter?
Cloud Security Posture Management (CSPM) is a technology that helps monitor and manage security across the cloud.

April 29, 2024
RAD Security
What is Cloud Security Posture Management (CSPM) and Why Does It Matter?
Cloud Security Posture Management (CSPM) is a technology that helps monitor and manage security across the cloud.
Cloud-Native Security
Security

April 29, 2024
The 10 Female Cybersecurity Founders You Need to Follow
With RSA approaching, here are some female founders and leaders to follow who are leveling the playing field in cybersecurity.

April 29, 2024
Brooke Motta
The 10 Female Cybersecurity Founders You Need to Follow
With RSA approaching, here are some female founders and leaders to follow who are leveling the playing field in cybersecurity.
No items found.

April 17, 2024
Kubernetes Version 1.30 Security Features
This Kubernetes version 1.30 includes many security related features that will help with admission control, authentication, authorization and more.

April 17, 2024
Story Tweedie-Yates
Kubernetes Version 1.30 Security Features
This Kubernetes version 1.30 includes many security related features that will help with admission control, authentication, authorization and more.
Kubernetes
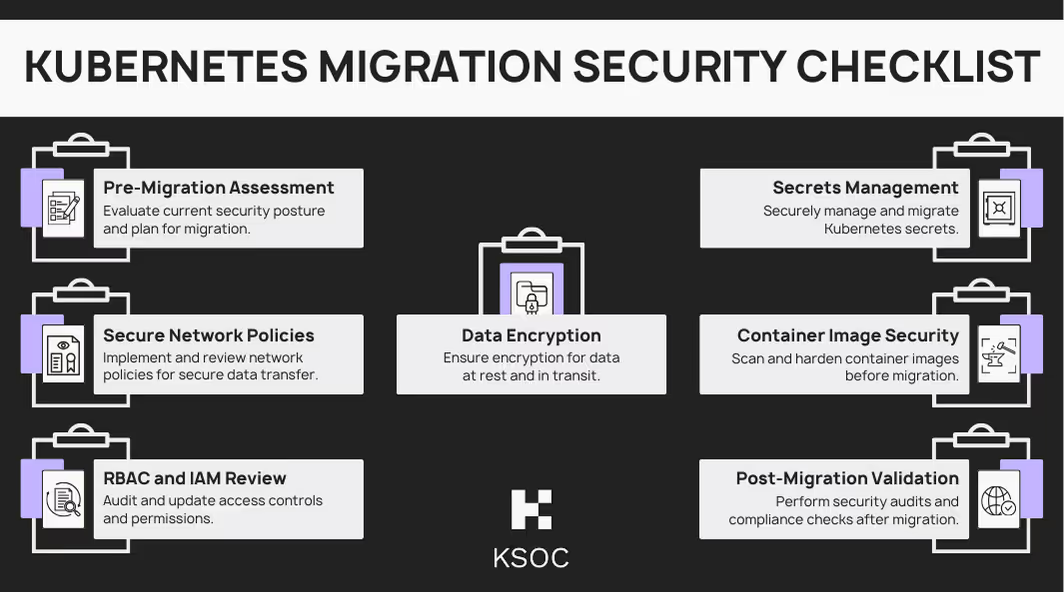
April 15, 2024
Kubernetes Migration Guide
Migrating to Kubernetes is a large undertaking and requires a security-first mindset to ensure that applications remain secure.

April 15, 2024
RAD Security
Kubernetes Migration Guide
Migrating to Kubernetes is a large undertaking and requires a security-first mindset to ensure that applications remain secure.
Kubernetes
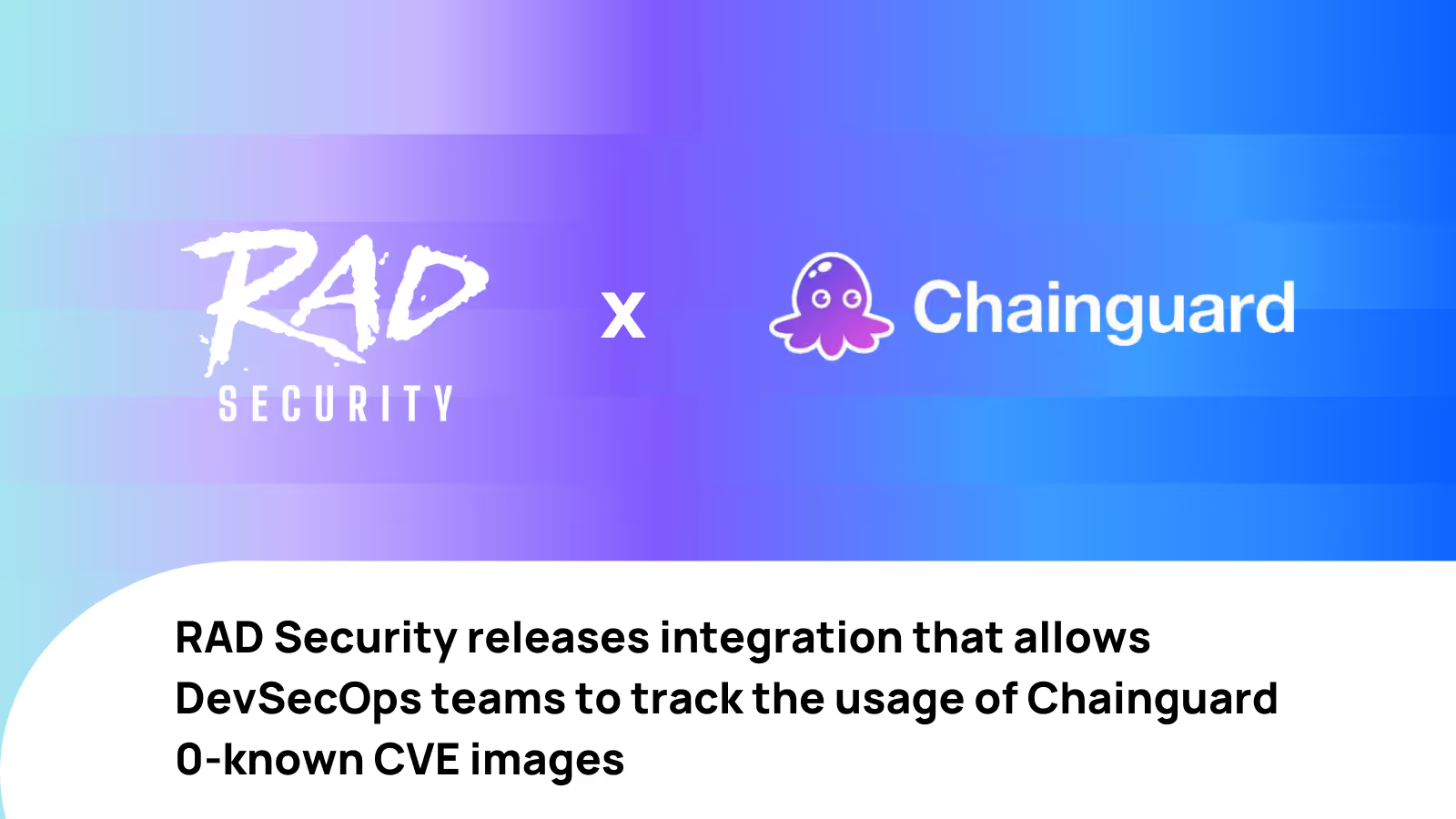
April 4, 2024
RAD Security Integrates with Chainguard to Strengthen CVE Vulnerability Management Systems
As part of RAD Security's real-time Kubernetes posture management solution, you can now automatically track, and even enforce, the usage of Chainguard’s low-to-zero known CVE container images.

April 4, 2024
Jimmy Mesta
RAD Security Integrates with Chainguard to Strengthen CVE Vulnerability Management Systems
As part of RAD Security's real-time Kubernetes posture management solution, you can now automatically track, and even enforce, the usage of Chainguard’s low-to-zero known CVE container images.
Containers

March 30, 2024
XZ Backdoor (CVE-2024-3094) - What You Need to Know
CVE-2024-3094, otherwise known as the XZ Backdoor software supply chain attack, is considered the most sophisticated social engineering attack on open-source projects to date.

March 30, 2024
Jimmy Mesta
XZ Backdoor (CVE-2024-3094) - What You Need to Know
CVE-2024-3094, otherwise known as the XZ Backdoor software supply chain attack, is considered the most sophisticated social engineering attack on open-source projects to date.
Cloud Attacks
Security
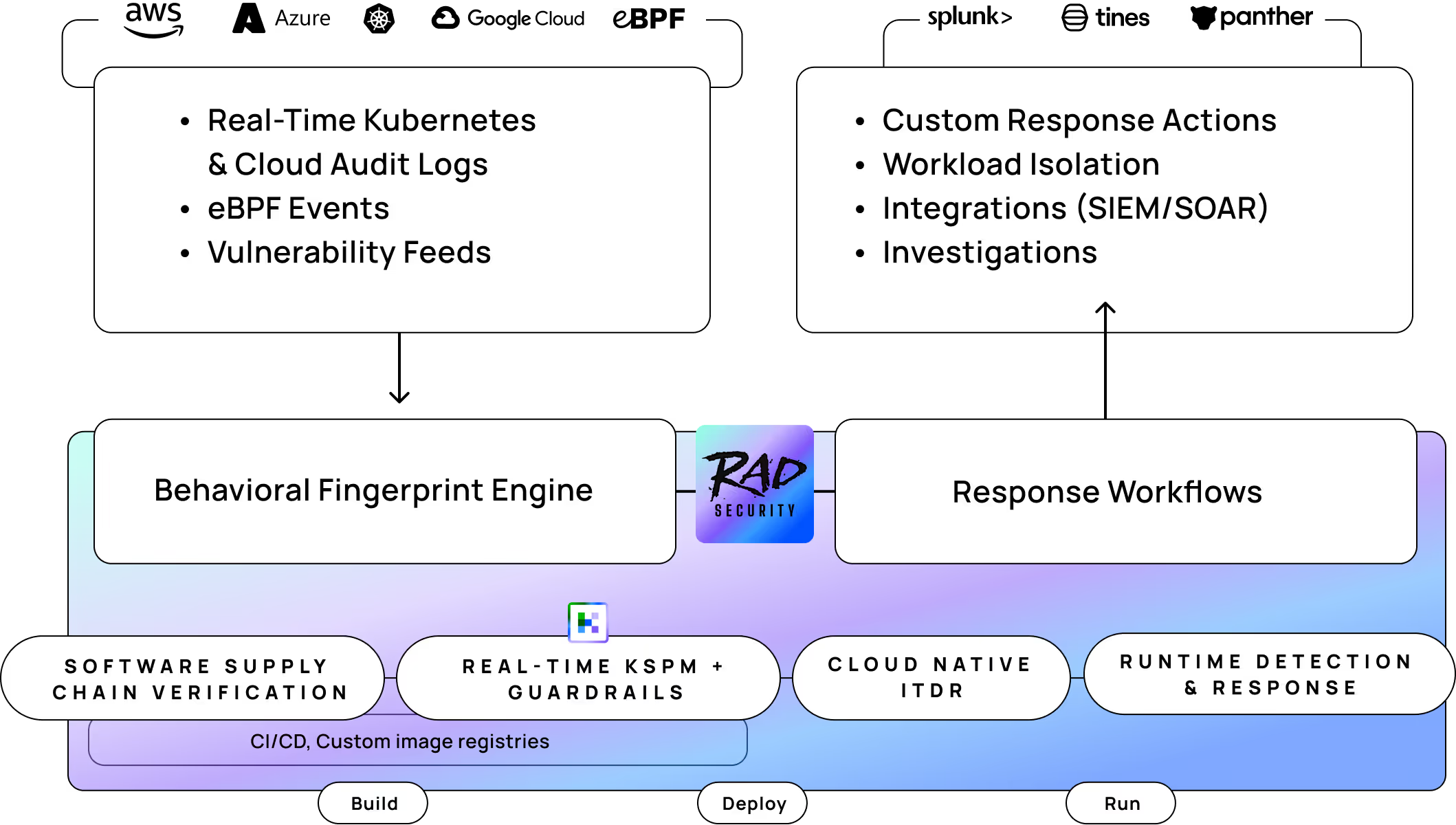
March 12, 2024
Reimagining Cloud Native Detection & Response: KSOC's Evolutionary Shift to RAD Security
KSOC has evolved to RAD Security, signifying a new era of behavioral cloud native detection and response that can combat today’s evolving threats.

March 12, 2024
Brooke Motta
Reimagining Cloud Native Detection & Response: KSOC's Evolutionary Shift to RAD Security
KSOC has evolved to RAD Security, signifying a new era of behavioral cloud native detection and response that can combat today’s evolving threats.
Cloud-Native Security
Detection and Response
News

March 12, 2024
Securing Your Future in 2024: Grabbing a Piece of the K8s Security Pie
Kubernetes security is like an open invitation to further your career and make yourself an invaluable part of your company’s journey forward.

March 12, 2024
Brooke Motta
Securing Your Future in 2024: Grabbing a Piece of the K8s Security Pie
Kubernetes security is like an open invitation to further your career and make yourself an invaluable part of your company’s journey forward.
Kubernetes
No resources match your criteria.



